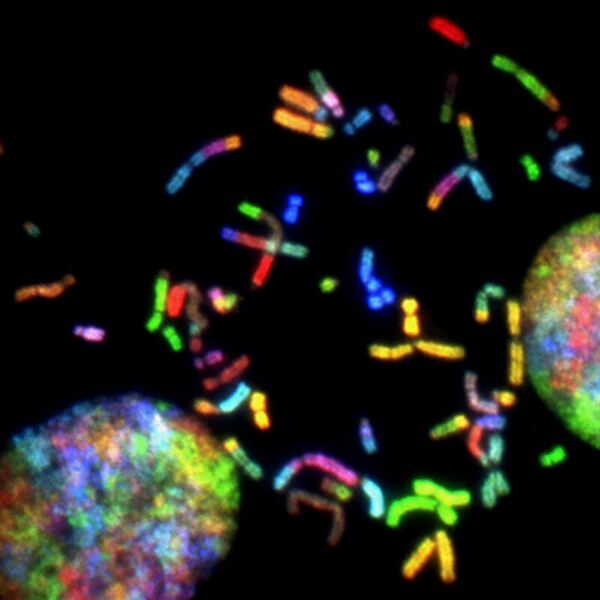
In this study, the authors investigate the effect of remote learning (due to the COVID-19 pandemic) on sleeping habits amongst teenagers in Ohio. Using survey results, sleep habits and attitudes toward school were assessed before and after the COVID-19 pandemic.
Read More...