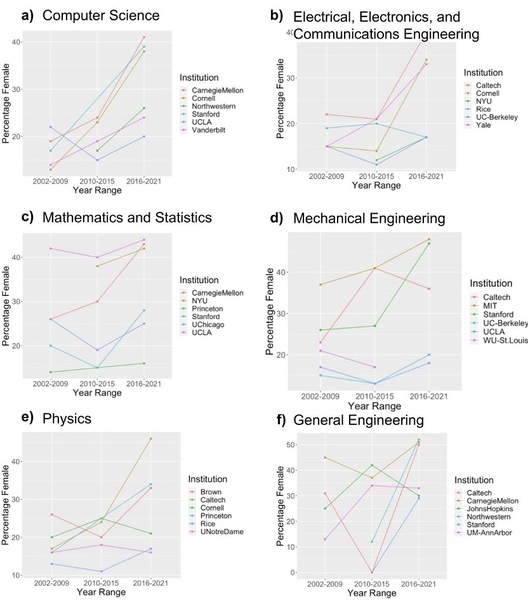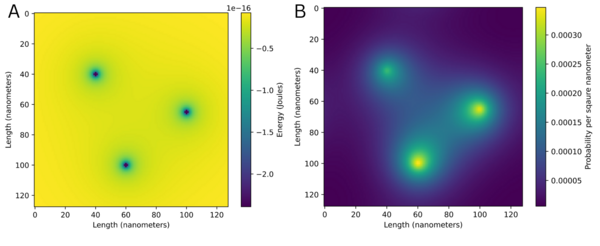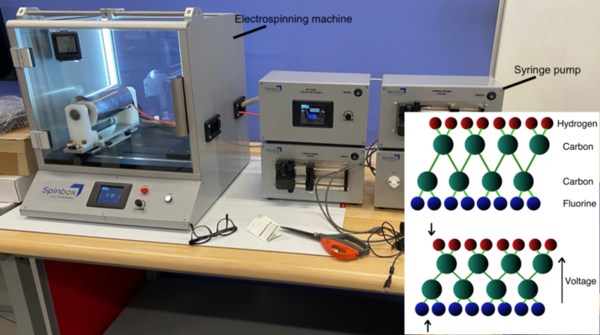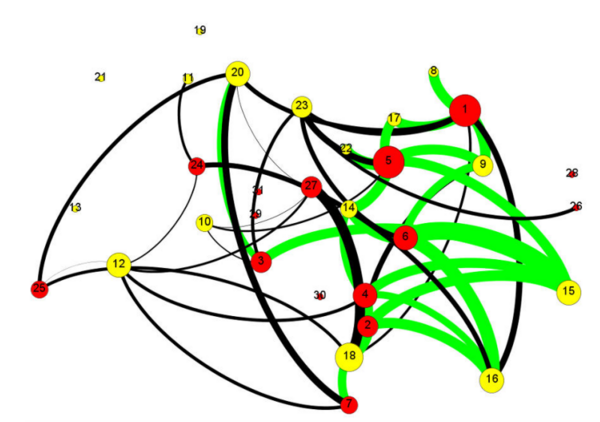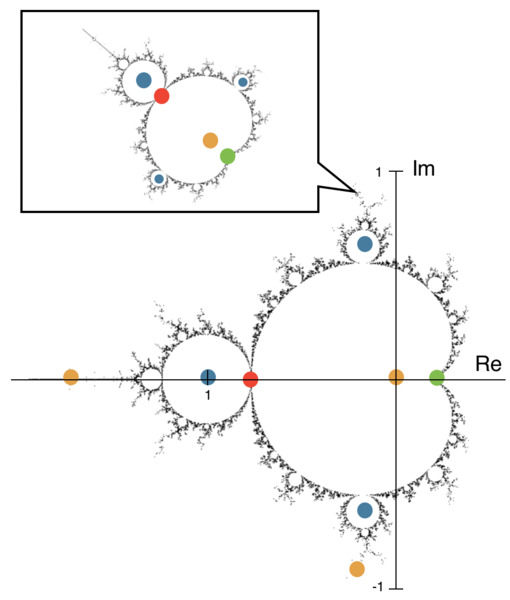
This study aimed to predict and explain chaotic behavior in the Mandelbrot Set, one of the world’s most popular models of fractals and exhibitors of Chaos Theory. The authors hypothesized that repeatedly iterating the Mandelbrot Set’s characteristic function would give rise to a more intricate layout of the fractal and elliptical models that predict and highlight “hotspots” of chaos through their overlaps. The positive and negative results from this study may provide a new perspective on fractals and their chaotic nature, helping to solve problems involving chaotic phenomena.
Read More...