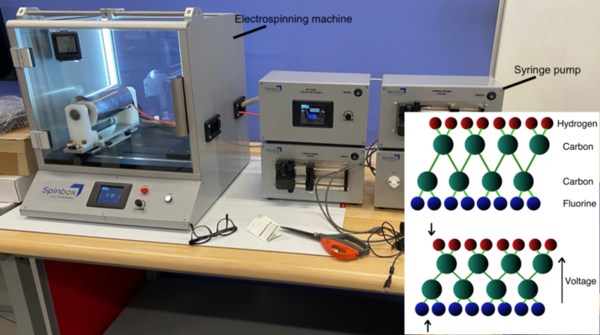
Greenspaces (urban and wetland areas that contain vegetation) are beneficial to reducing pollution, while airplanes are a highly-polluting method of transportation. The authors examine the intersection of these two environmental factors by processing satellite images to reveal what percentage of flight paths go over greenspaces at major US airports.
Read More...