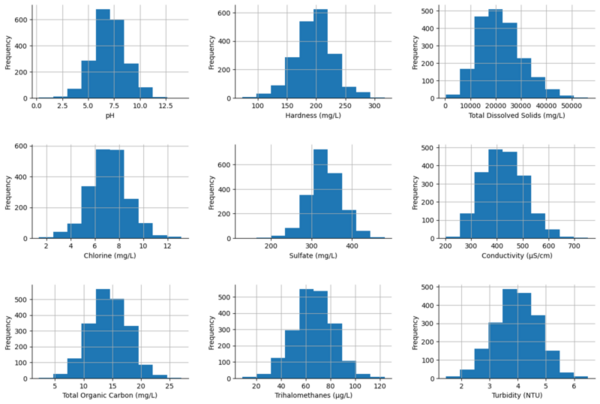
There have been several issues concerning the water quality in Ulaanbaatar, Mongolia in the past few years. This study, we collected 28 samples from 6 districts of Ulaanbaatar to check if the water supply quality met the standards of the World Health Organization, the Environmental Protection Agency, and a Mongolian National Standard. Only three samples fully met all the requirements of the global standards. Samples in Zaisan showed higher hardness (>120 ppm) and alkalinity levels (20–200 ppm) over the other districts in the city. Overall, the results show that it is important to ensure a safe and accessible water supply in Ulaanbaatar to prevent future water quality issues.
Read More...