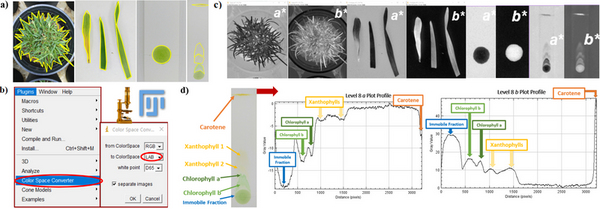
Overwatering and underwatering grass are widespread issues with environmental and financial consequences. This study developed an accessible method to assess grass water use efficiency (WUE) combining smartphone imaging with open access color unmixing analysis. The method can be applied in automated irrigation systems or apps, providing grass WUE assessment for regular consumer use.
Read More...