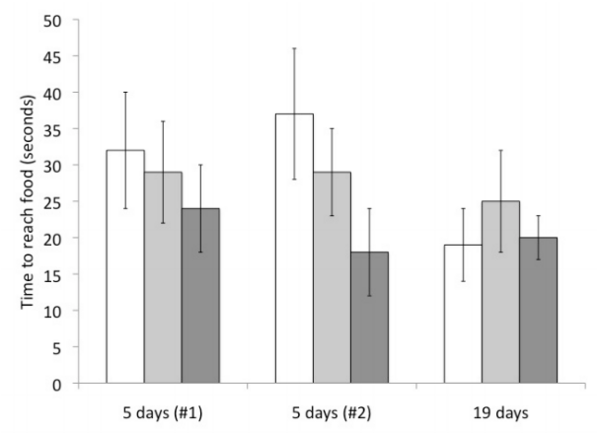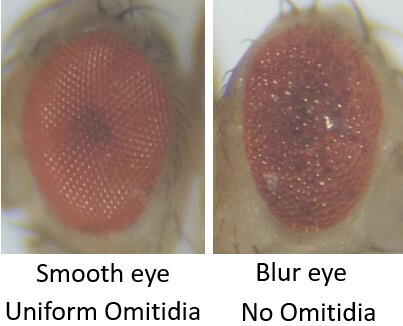
In this work, the authors compared the effects of common natural products, including sesame, cinnamon, garlic, moringa and turmeric on tumor growth in Drosophila eyes. The data showed that these natural products cannot be used to reduce tumor growth once it has completely formed. However, the data suggested that some natural products can reduce cancer cell growth when tumors are treated early.
Read More...