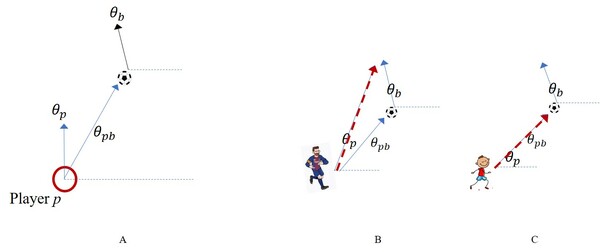
In this article, the authors use datasets of professional and youth soccer players' movements to map and statistically compare them. Analysis compared movements that led to goals or no-goals and differences between pros and youth.
Read More...Understanding the movement of professional and high school soccer players

In this article, the authors use datasets of professional and youth soccer players' movements to map and statistically compare them. Analysis compared movements that led to goals or no-goals and differences between pros and youth.
Read More...Population Forecasting by Population Growth Models based on MATLAB Simulation
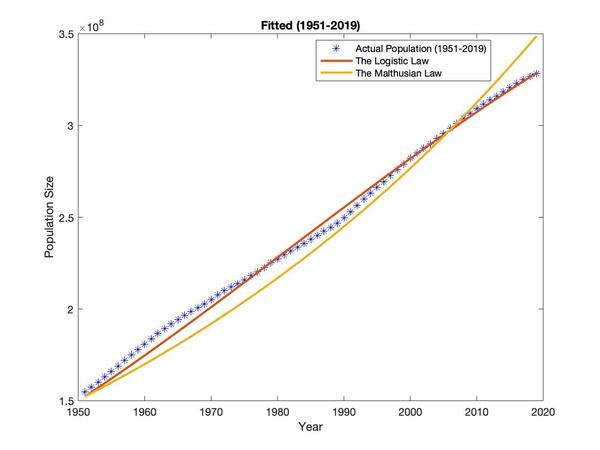
In this work, the authors investigate the accuracy with which two different population growth models can predict population growth over time. They apply the Malthusian law or Logistic law to US population from 1951 until 2019. To assess how closely the growth model fits actual population data, a least-squared curve fit was applied and revealed that the Logistic law of population growth resulted in smaller sum of squared residuals. These findings are important for ensuring optimal population growth models are implemented to data as population forecasting affects a country's economic and social structure.
Read More...Fractal dimensions of crumpled paper

Here, beginning from an interest in fractals, infinitely complex shapes. The authors investigated the fractal object that results from crumpling a sheet of paper. They determined its fractal dimension using continuous Chi-squared analysis, thereby testing and validating their model against the more conventional least squares analysis.
Read More...Comparing the performance of lateral control algorithms on long rigid vehicles in urban environments
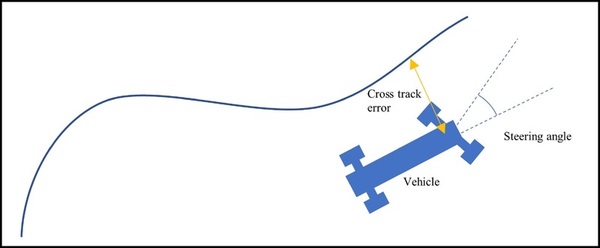
Here, seeking to better understand the control algorithms used in autonomous vehicles, the authors compared the Stanley and pure pursuit control algorithms along with a new version of each. Unexpectedly, they found that no control algorithm offered optimal performance, but rather resulted in tradeoffs between the various ideal results.
Read More...Open string vibrato: does it exist?
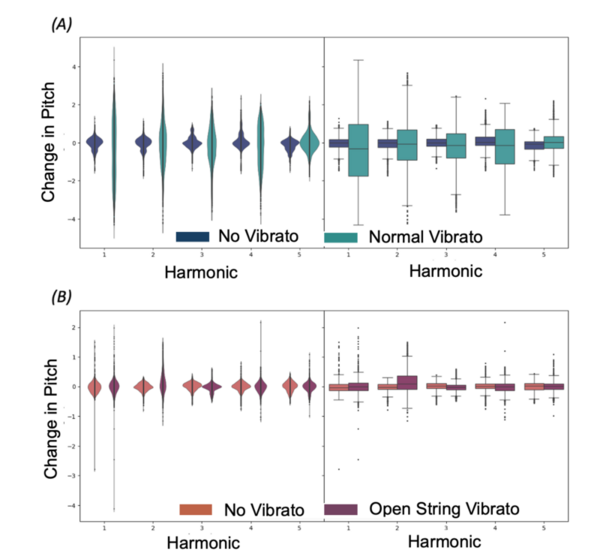
Vibrato, defined as a rapid and subtle oscillation in pitch, is a technique that is commonly used by musicians to add expression and colour to notes. However, on stringed instruments, there are certain notes (open string notes) on which it is impossible to perform the technique. Without vibrato, they can sound angular and unpleasant, especially when juxtaposed against other notes played with vibrato. String players therefore use an alternative to achieve the same vibrato effect on the open string — a technique referred to as “open string vibrato”. While the technique is widely used, it is unknown how much of a physical effect it has on the sound waves produced, if any at all. The purpose of this study is to analyse open string vibrato using a statistical approach to provide evidence to characterize the physical effect of the technique, and then compare it to normal vibrato. We hypothesised that it would have a noticeable and measurable effect on the sound waves produced because of the technique’s widespread usage. To test this, notes, with and without either open string vibrato or normal vibrato, were recorded on the violin. We analyzed the audio recordings using a computational and statistical approach. The results of the study partially agreed with our hypothesis: while the technique has an observable physical effect on the sound waves, the effect is weaker than expected. We concluded that open string vibrato does work, but has quite a subtle effect, and thus should only be used when there is no other option.
Read More...Quantitative definition of chemical synthetic pathway complexity of organic compounds
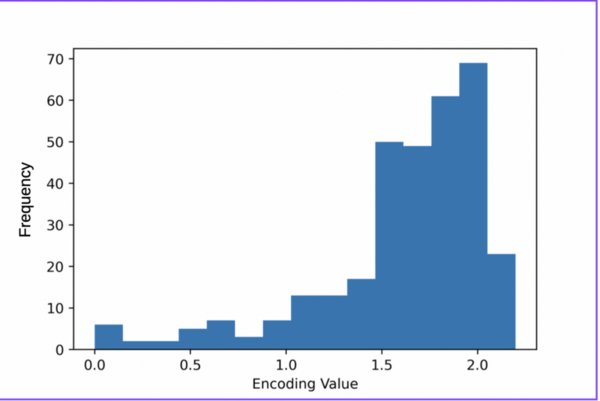
Irrespective of the final application of a molecule, synthetic accessibility is the rate-determining step in discovering and developing novel entities. However, synthetic complexity is challenging to quantify as a single metric, since it is a composite of several measurable metrics, some of which include cost, safety, and availability. Moreover, defining a single synthetic accessibility metric for both natural products and non-natural products poses yet another challenge given the structural distinctions between these two classes of compounds. Here, we propose a model for synthetic accessibility of all chemical compounds, inspired by the Central Limit Theorem, and devise a novel synthetic accessibility metric assessing the overall feasibility of making chemical compounds that has been fitted to a Gaussian distribution.
Read More...Optimizing airfoil shape for small, low speed, unmanned gliders: A homemade investigation

Here, the authors sought to identify a method to optimize the lift generated by an airfoil based solely on its shape. By beginning with a Bernoullian model to predict an optimized wing shape, the authors then tested their model against other possible shapes by constructing them from Styrofoam and testing them in a small wind tunnel. Contrary to their hypothesis, they found their expected optimal airfoil shape did not result in the greatest lift generation. They attributed this to a variety of confounding variables and concluded that their results pointed to a correlation between airfoil shape and lift generation.
Read More...A novel approach to determine which organism best displays Gijswijt's Sequence in its genome
The sequence of nitrogenous bases that make up the DNA of organisms can contain hidden mathematical sequences. Here the authors used BioPython, a programming tool, to find an organism that displays Gijswijt’s Sequence in its genome. In this manner they found that the common carp best displays Gijswijt’s Sequence in its genome.
Read More...Optimizing Interplanetary Travel Using a Genetic Algorithm

In this work, the authors develop an algorithm that solves the problem of efficient space travel between planets. This is a problem that could soon be of relevance as mankind continues to expand its exploration of outer space, and potentially attempt to inhabit it.
Read More...A Retrospective Statistical Analysis of Second Primary Cancers in the Delmarva Peninsula, U.S.A.

A significant percentage of cancer survivors develop a second primary cancer. Using data of deceased patients provided by the Peninsula Regional Medical Center, Li and Holdai conducted a retrospective statistical analysis to investigate whether the type of the first cancer affects the occurrence time and type of the second primary cancer.
Read More...