
The authors looked at different algorithms and their ability to encrypt and decrypt text of various lengths.
Read More...Comparative analysis of the speeds of AES, ChaCha20, and Blowfish encryption algorithms

The authors looked at different algorithms and their ability to encrypt and decrypt text of various lengths.
Read More...LawCrypt: Secret Sharing for Attorney-Client Data in a Multi-Provider Cloud Architecture
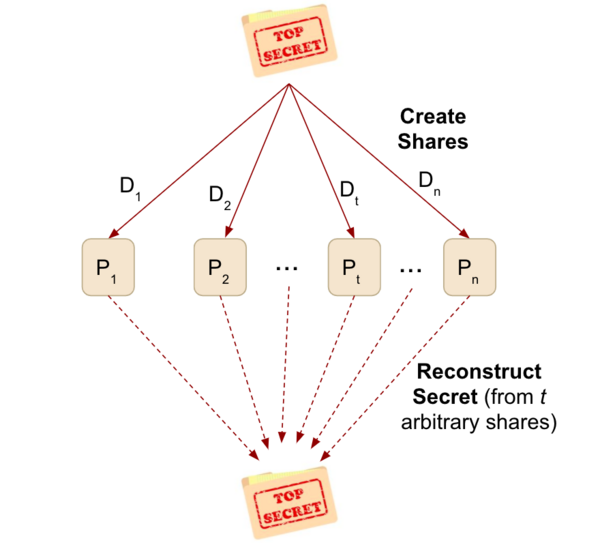
In this study, the authors develop an architecture to implement in a cloud-based database used by law firms to ensure confidentiality, availability, and integrity of attorney documents while maintaining greater efficiency than traditional encryption algorithms. They assessed whether the architecture satisfies necessary criteria and tested the overall file sizes the architecture could process. The authors found that their system was able to handle larger file sizes and fit engineering criteria. This study presents a valuable new tool that can be used to ensure law firms have adequate security as they shift to using cloud-based storage systems for their files.
Read More...A meta-analysis on NIST post-quantum cryptographic primitive finalists
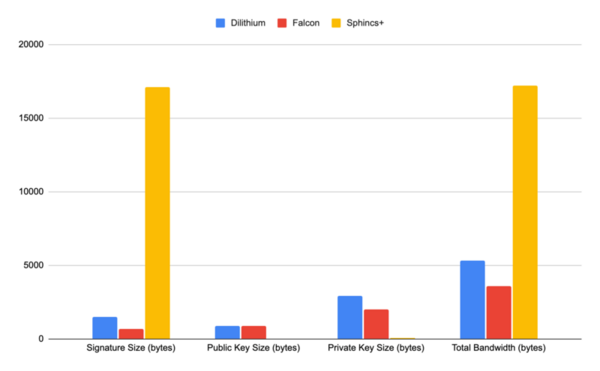
The advent of quantum computing will pose a substantial threat to the security of classical cryptographic methods, which could become vulnerable to quantum-based attacks. In response to this impending challenge, the field of post-quantum cryptography has emerged, aiming to develop algorithms that can withstand the computational power of quantum computers. This study addressed the pressing concern of classical cryptographic methods becoming vulnerable to quantum-based attacks due to the rise of quantum computing. The emergence of post-quantum cryptography has led to the development of new resistant algorithms. Our research focused on four quantum-resistant algorithms endorsed by America’s National Institute of Standards and Technology (NIST) in 2022: CRYSTALS-Kyber, CRYSTALS-Dilithium, FALCON, and SPHINCS+. This study evaluated the security, performance, and comparative attributes of the four algorithms, considering factors such as key size, encryption/decryption speed, and complexity. Comparative analyses against each other and existing quantum-resistant algorithms provided insights into the strengths and weaknesses of each program. This research explored potential applications and future directions in the realm of quantum-resistant cryptography. Our findings concluded that the NIST algorithms were substantially more effective and efficient compared to classical cryptographic algorithms. Ultimately, this work underscored the need to adapt cryptographic techniques in the face of advancing quantum computing capabilities, offering valuable insights for researchers and practitioners in the field. Implementing NIST-endorsed quantum-resistant algorithms substantially reduced the vulnerability of cryptographic systems to quantum-based attacks compared to classical cryptographic methods.
Read More...Design and implementation of a cryptographically secure electronic voting infrastructure
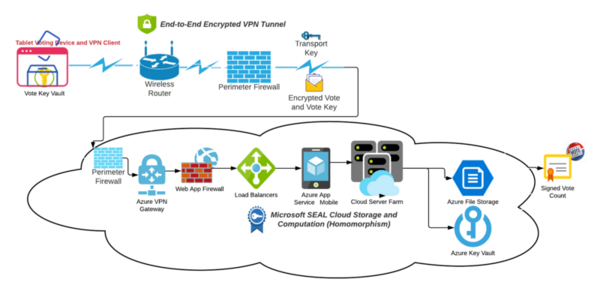
In this study, the authors present proposed cryptographic controls for election sites with the hypothesis that this will mitigate risk and remediate vulnerabilities.
Read More...Blockchain databases: Encrypted for efficient and secure NoSQL key-store
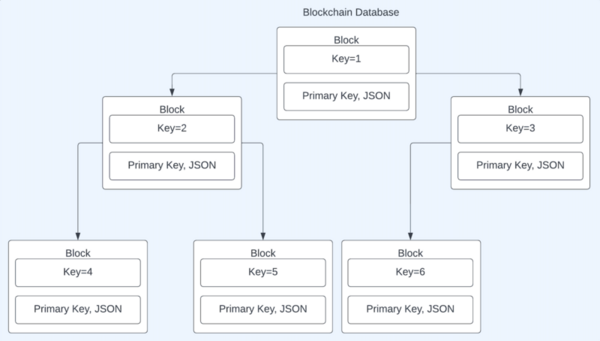
Although commonly associated with cryptocurrency, blockchains offer security that other databases could benefit from. These student authors tested a blockchain database framework, and by tracking runtime of four independent variables, they prove this framework is feasible for application.
Read More...An improved video fingerprinting attack on users of the Tor network
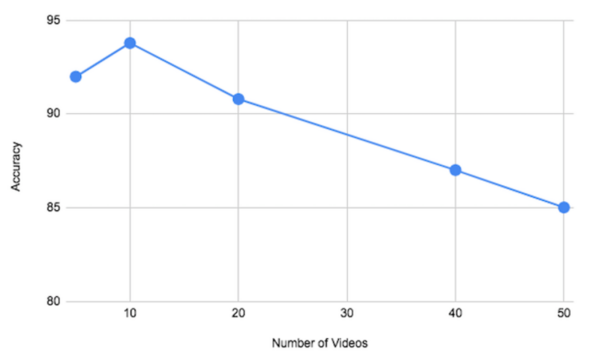
The Tor network allows individuals to secure their online identities by encrypting their traffic, however it is vulnerable to fingerprinting attacks that threaten users' online privacy. In this paper, the authors develop a new video fingerprinting model to explore how well video streaming can be fingerprinted in Tor. They found that their model could distinguish which one of 50 videos a user was hypothetically watching on the Tor network with 85% accuracy, demonstrating that video fingerprinting is a serious threat to the privacy of Tor users.
Read More...