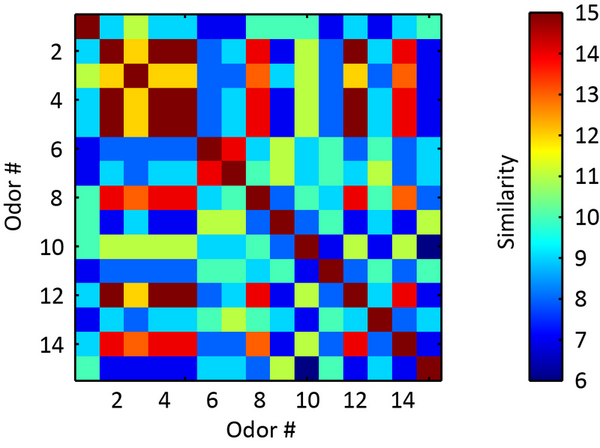
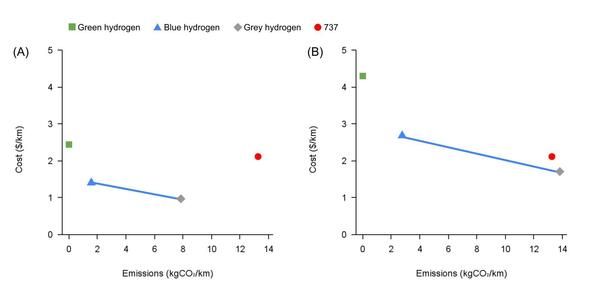
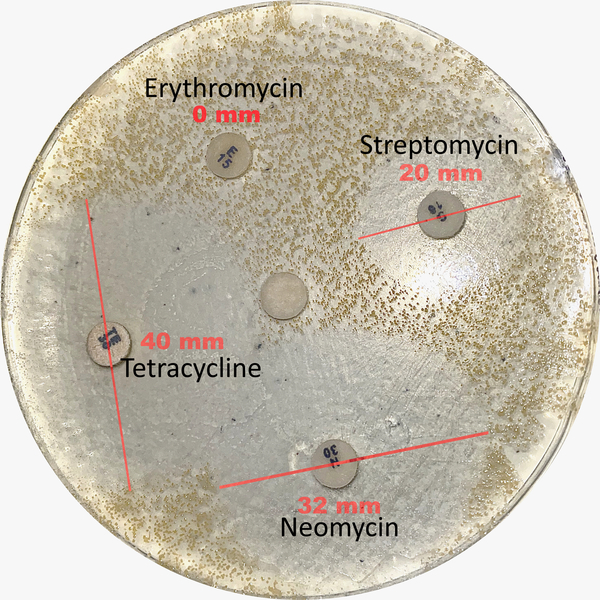
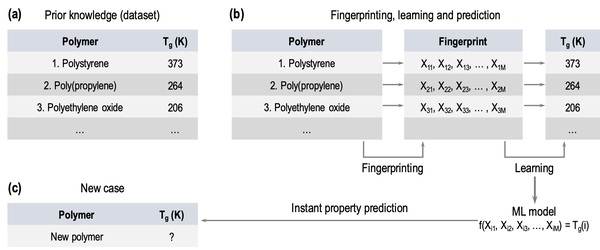
With monitoring of climate change and the evolving properties of the atmosphere more critical than ever, the authors of this study take sea salt aerosols into consideration. These sea salt aerosols, sourced from the bubbles found at the surface of the sea, serve as cloud condensation nuclei (CCN) and are effective for the formation of clouds, light scattering in the atmosphere, and cooling of the climate. With amines being involved in the process of CCN formation, the authors explore the effects of alkylamines on the properties of sea salt aerosols and their potential relevance to climate change.
Read More...