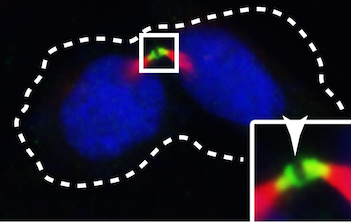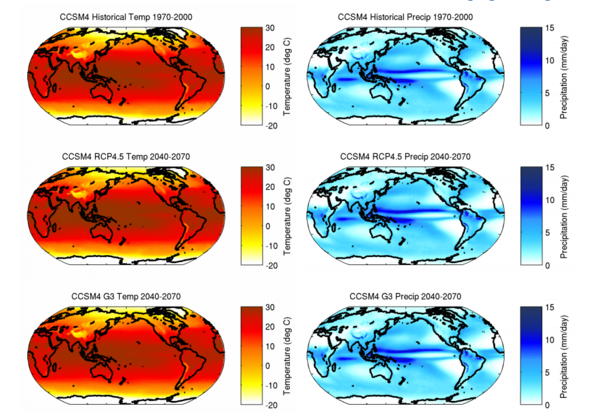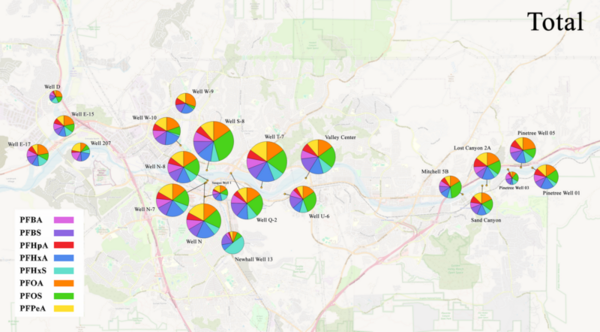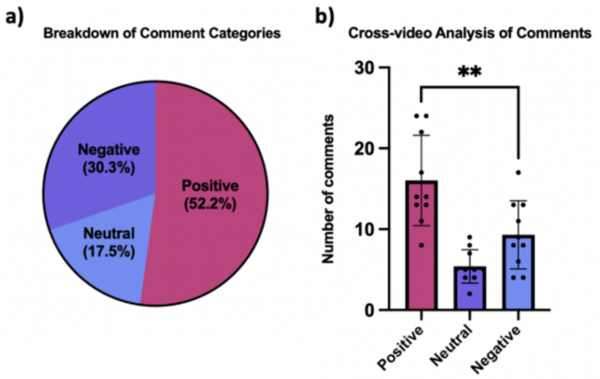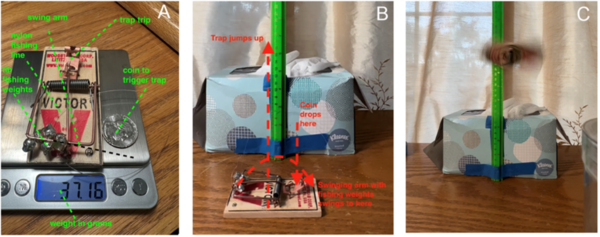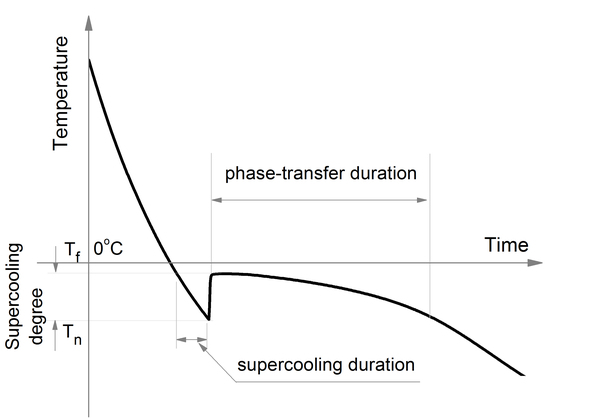
In this article, the authors investigate whether coolant temperature affects soil cooling curves of soil with otherwise identical properties. The coolant temperature is representative of environmental temperature, and the authors hypothesized that differences in this temperature would not affect the freezing temperature of soil. Their findings validated their hypothesis providing helpful information relevant to understanding how frost heaves happen and how to predict their occurrence more accurately.
Read More...